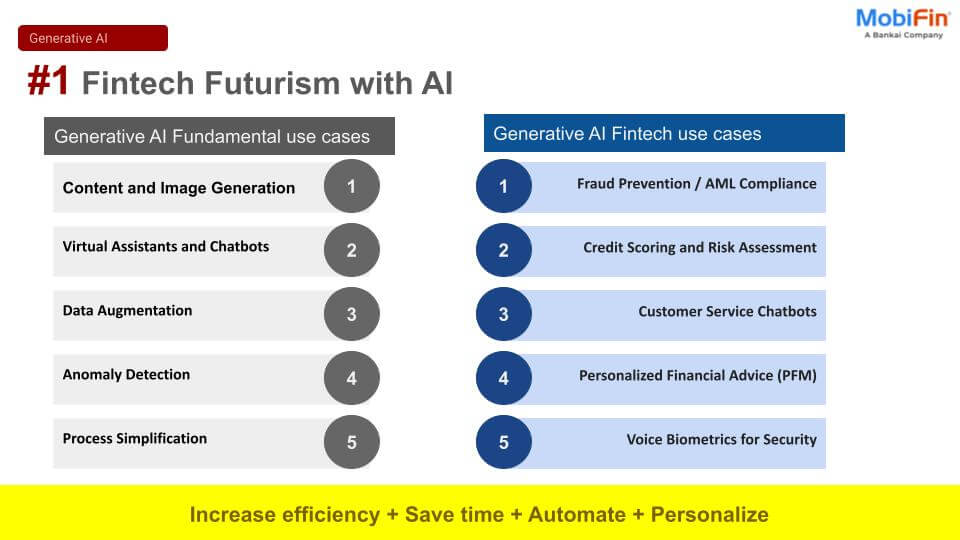
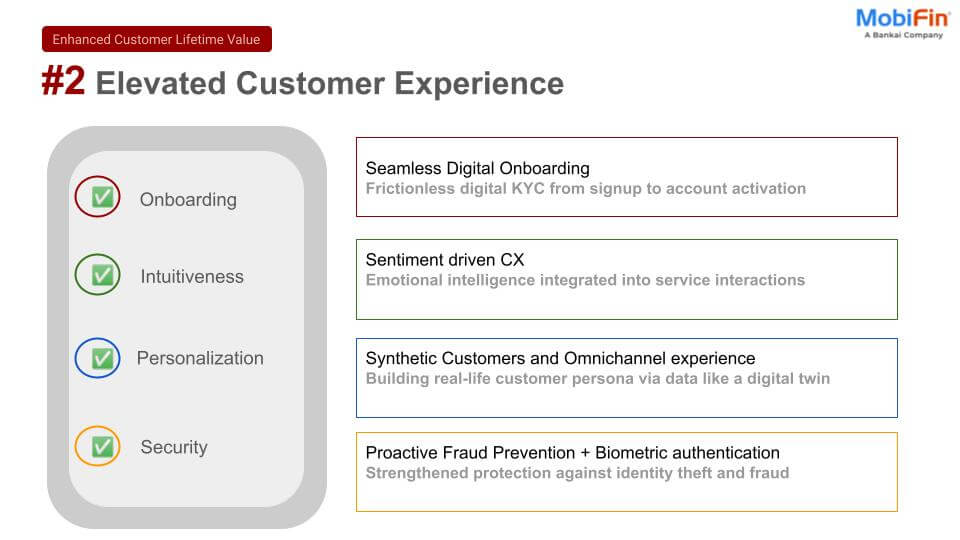
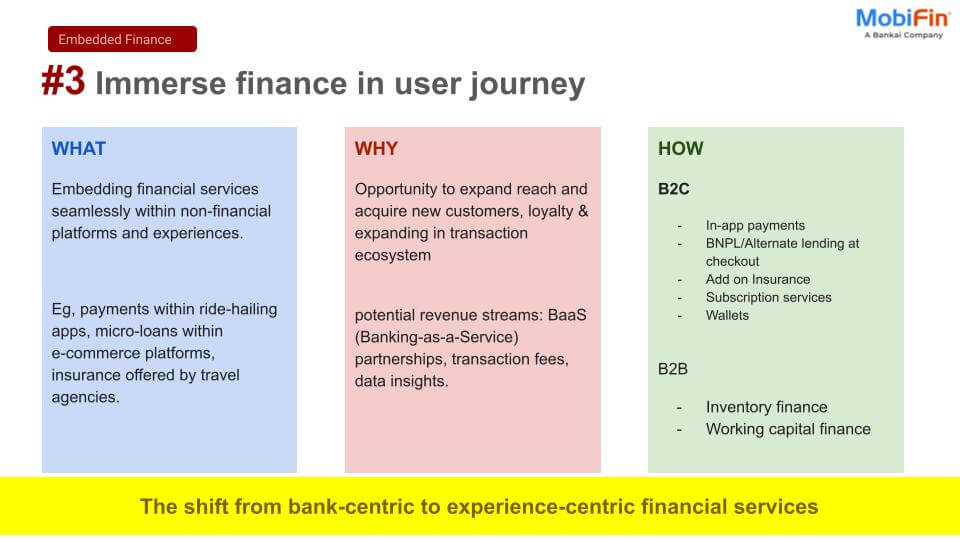
Introduction
Digital wallets have moved from being a convenience layer to becoming core financial infrastructure in many markets. What started as simple stored-value instruments are now handling billions of micro-transactions, instant merchant settlements, peer-to-peer transfers, government disbursements, and increasingly complex cross-border flows. In many high-growth regions, wallets are often the first formal financial product a user interacts with, making them both a driver of inclusion and a magnet for abuse.
According to recent industry estimates, global digital wallet users are expected to exceed 5.2 billion globally in 2026 up from 3.4 billion in 2022. It reflects growth of more than 53%.
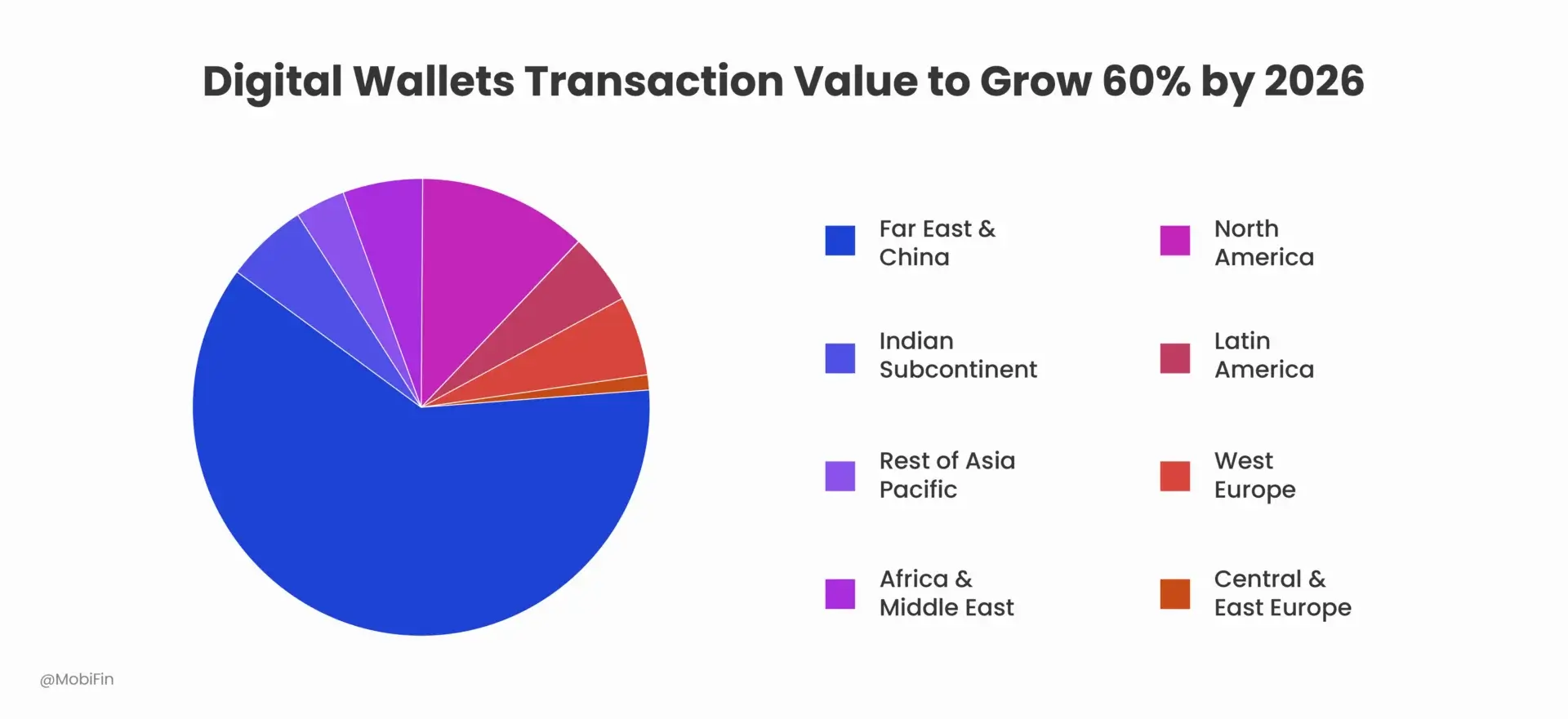
This scale fundamentally alters the fraud landscape. In this context, “high-volume” does not simply mean a large user base. It refers to ecosystems processing millions of low-value transactions daily, where risk decisions must be rendered in milliseconds and trust is established progressively rather than upfront. At this velocity, fraud is not episodic. It is systemic.
High-volume wallet ecosystems operate on different economic, technical, and behavioral dynamics than traditional card-based systems. Transactions are smaller but far more frequent. Decisions must be made in milliseconds. Trust is often established progressively rather than upfront. And the ecosystem extends well beyond the wallet user to agents, merchants, partners, APIs, and third-party integrators.
Fraud in card systems typically revolves around credential theft, chargebacks, and post-transaction dispute management. Wallet fraud, by contrast, is more diverse and systemic. It includes synthetic identities, account takeovers, mule networks, agent collusion, velocity abuse, bonus farming, laundering through peer networks, and exploitation of operational gaps. The attack surface is broader, and the consequences of delay are more severe.
At the center of all this lies persistent tension. Wallet operators are under constant pressure to deliver speed, convenience, and low friction to drive adoption and inclusion. At the same
time, they must maintain strong controls to protect funds, comply with regulations, and preserve trust. Optimizing one at the expense of the other almost always fails.
At scale, the cost of imbalance becomes material. Excessive friction suppresses genuine transaction volume and weakens agent economics. Insufficient control leads to incentive leakage, synthetic account farming, and cumulative micro-fraud that erodes margins silently over time. The challenge is not eliminating fraud entirely but keeping it economically neutral while preserving growth velocity.
This is why fraud prevention in high-volume wallet ecosystems is an architectural problem rather than a tooling problem. The effectiveness of fraud controls depends less on the number of tools deployed and more on how deeply fraud intelligence is embedded into the wallet’s core rails, workflows, and decision-making fabric.
Tool-based stacks often create fragmented visibility, where onboarding systems, transaction monitoring engines, and operational controls operate independently. Architectural fraud control, by contrast, ensures that identity signals, behavioral patterns, device intelligence, and ecosystem relationships inform each other continuously rather than in isolation.
Why traditional fraud controls fail at wallet scale
Many wallet programs inherit fraud approaches from banking or card environments. These approaches often break down once transaction volumes surge and ecosystem complexity increases.
The first limitation is an over-reliance on static rules. Fixed thresholds and deterministic rules struggle to keep up with adaptive fraud patterns. Fraudsters test limits, observe responses, and evolve quickly. What works at launch becomes ineffective within weeks in a live, high-volume environment.
Latency is another critical constraint. Wallet transactions are expected to complete in sub-second timeframes. Traditional fraud engines that rely on synchronous calls to multiple external systems introduce delays that directly impact user experience. In wallets, even small delays can cause transaction abandonment or operational bottlenecks at scale.
Risk ownership is also often fragmented. Onboarding teams manage KYC and identity checks. Payments teams focus on transaction monitoring. Operations handle disputes and reversals. When these functions operate in silos, critical signals are missed. A risky onboarding pattern may never be connected to downstream transaction abuse, and settlement anomalies may not feed back into real-time controls.
Siloed systems create blind spots. Each system sees only a slice of the user or transaction lifecycle. Fraud, however, exploits the seams between systems. When identity, device, transaction, and ecosystem data are not correlated in real time, fraudsters gain room to operate.
Fraud rarely exploits a single weakness. It exploits transitions between systems. When identity risk does not inform transaction limits, when agent anomalies do not influence settlement timing, or when incentive abuse signals do not adjust behavioral scoring, fraud gains structural advantage.
At wallet scale, these weaknesses compound quickly. The result is either uncontrolled fraud leakage or overly aggressive controls that harm genuine users and partners.
The modern wallet fraud surface
Effective fraud prevention starts with understanding the full fraud surface, not just individual transactions. In high-volume digital wallet ecosystems, risk emerges across multiple layers of the ecosystem.
Onboarding and identity layers are the first line of defense. Fraud often begins with compromised, synthetic, or recycled identities designed to pass minimal checks and later exploit transactional limits or incentives.
Device and session layers provide critical behavioral context. Multiple accounts sharing devices, emulators, or anomalous session patterns are common indicators of coordinated abuse.
Funding and cash-in channels introduce their own risks. Bank transfers, cards, vouchers, and agent-assisted cash-ins each carry different fraud vectors and operational dependencies.
Peer-to-peer and merchant payments are frequently abused for laundering, circular transactions, and velocity-based attacks. Small amounts spread across networks can mask large-scale fraud.
Agent networks are both enablers of inclusion and sources of systemic risk. Agent impersonation, float abuse, collusion, and fake transactions can undermine entire regions if not monitored holistically.
In agent-heavy ecosystems, fraud often manifests through coordinated float manipulation, artificial transaction inflation, or circular settlement flows. Monitoring agents in isolation is insufficient. Network-level intelligence is required to detect structural abuse.
Withdrawals and cross-border flows amplify impact. Fraud that enters the system cheaply can exit through higher-value or harder-to-recover channels. To put things into a better perspective, cross-border payment fraud increased 20% on a year-on-year basis, with more than US$50 billion in confirmed actual fraud from US$1.5 trillion in flagged transactions.
Finally, APIs and partner ecosystems expand the attack surface beyond the wallet’s direct control. Third-party integrations, promotions, and embedded finance use cases introduce new vectors that must be governed consistently.
Mapping this ecosystem end to end is a prerequisite for meaningful fraud control. Without this end-to-end mapping, operators often respond reactively by tightening controls after losses surface rather than anticipating systemic patterns. In high-volume environments, reactive control is expensive. Preventive architecture is economically superior.
Core pillars of fraud prevention in high-volume ecosystems
Identity and behavioral integrity
In high-volume wallets, identity is not a one-time check. It is an evolving construct.
Progressive KYC allows operators to balance inclusion with risk. Users start with limited functionality and earn higher limits as trust increases. This approach reduces upfront friction while containing exposure.
Device fingerprinting adds a persistent layer of context that complements identity data. Even when credentials change, device-level signals help detect reuse, sharing, or automation.
Behavioral biometrics analyze how users interact with the app. Typing patterns, navigation behavior, and gesture dynamics can distinguish genuine users from scripted or coerced activity.
Velocity and anomaly detection across identity attributes help surface coordinated behavior. Sudden spikes in account creation, similar profiles, or synchronized actions often indicate organized fraud.
Together, these controls focus not just on who the user claims to be, but on whether their behavior aligns with expected patterns over time.
Transactional intelligence
At scale, every transaction must be evaluated in context.
Real-time risk scoring combines multiple signals into a single decisioning framework. Rather than binary allow-or-block outcomes, risk scores enable nuanced responses.
These responses may include dynamic limit adjustments, delayed settlement, stepped-up verification, or adaptive friction rather than outright rejection. This flexibility is critical in ecosystems where outright declines can damage trust and suppress legitimate usage.
Pattern recognition identifies sequences that may appear benign in isolation but are risky in aggregate. Repeated small transfers, circular flows, or time-based patterns are common examples.
Peer-group analysis compares user behavior against relevant cohorts. A transaction that is normal for one segment may be highly anomalous for another.
Contextual decisioning ensures that decisions consider intent, history, channel, and downstream impact. The same transaction may warrant different actions depending on where it occurs in the user journey.
Ecosystem controls
Fraud rarely operates in isolation at wallet scale. Networks matter.
Agent risk scoring evaluates agents not just individually but in relation to their peers and regions. Sudden deviations in volume, timing, or customer mix can signal issues early.
Merchant trust tiers align controls with risk. Established merchants may enjoy smoother flows, while new or high-risk categories face tighter monitoring.
Network graph analysis uncovers relationships between users, devices, agents, and merchants. These graphs are essential for identifying mule networks and coordinated abuse.
Collusion detection focuses on patterns that suggest cooperation rather than individual misconduct, which is often the case in large-scale fraud operations.
Operational parameters
Even the best detection is ineffective without strong operational execution.
Automated actions allow systems to respond instantly at scale, freezing accounts, adjusting limits, or flagging transactions without human intervention.
Human review workflows remain essential for edge cases and learning loops. The key is to design them for efficiency and feedback, not bottlenecks.
Adaptive friction introduces challenges only when risk is elevated. This preserves user experience while increasing security where needed.
Explainability is critical for compliance, trust, and internal alignment. Teams must understand why decisions were made and be able to justify them to regulators and partners.
Designing fraud systems for volume, not exceptions
Many fraud systems are designed around investigating rare, high-value incidents. High-volume wallets require the opposite mindset.
Event-driven architectures allow fraud logic to react to streams of activity rather than isolated requests. Every login, transaction, and state change becomes an input into the risk model.
Stream-based decisioning enables continuous assessment rather than one-time checks. Risk evolves as new information arrives.
Asynchronous investigations decouple detection from resolution. Transactions can proceed with controls in place while deeper analysis happens in parallel.
Stateful risk engines maintain memory across sessions and transactions. This historical awareness is essential for understanding trajectories rather than snapshots.
Audit-first data models ensure that every decision, signal, and outcome is recorded. This supports compliance, learning, and continuous improvement.
Most importantly, fraud prevention must be built into the wallet rails themselves. When fraud logic exists outside core flows as an external checkpoint, it introduces latency, fragmentation, and governance complexity. Embedded controls allow risk assessment to occur as part of normal state transitions (account creation, limit upgrades, fund movement, settlement, and reward issuance) without destabilizing transaction velocity.
What leading wallet operators are doing differently
Operators that succeed at scale share several characteristics.
They implement progressive trust frameworks that align user privileges with demonstrated behavior rather than static profiles.
They design risk-based user experiences, where friction is proportional and contextual rather than uniform.
They treat fraud as a product function, involving product, engineering, and operations teams in its evolution rather than relegating it to compliance alone.
They invest in shared intelligence layers that serve multiple use cases, from onboarding to payments to lending, reducing duplication and inconsistency.
They simulate changes before deployment. New rules, limits, or flows are tested against historical and synthetic data to understand impact before going live.
From fraud prevention to fraud engineering
Fraud will never disappear. In dynamic, high-volume ecosystems, it is a constant adversary. The goal is not elimination but control.
When fraud is engineered properly, losses are predictable, contained, and economically neutralized. Controls scale with growth rather than lag behind it. High-volume digital wallets that win treat fraud as infrastructure. It is designed, tested, monitored, and evolved with the same rigor as payments, ledgers, and settlement systems.
Conclusion
High-volume wallet ecosystems do not fail because fraud exists. They fail when fraud is treated as an afterthought rather than as core infrastructure. The operators that scale sustainably are those that engineer fraud controls into identity, transactions, ecosystem governance, and operational workflows from day one. They accept that fraud will evolve, and they design systems that evolve faster.
For institutions building or scaling digital wallet programs, the question is no longer whether to invest in fraud prevention, but how to architect it correctly across the full lifecycle. MobiFin enables this through a unified orchestration approach that embeds fraud logic across onboarding, wallet management, payments, lending, and rewards. Instead of stitching together disconnected tools, institutions can manage risk through centralized workflows, versioned rules, AI-driven intelligence, and audit-ready controls that scale with volume.
If you are planning to launch, expand, or modernize a high-volume wallet ecosystem, now is the time to rethink fraud as engineered infrastructure and talk to MobiFin experts.
Book a demo now to explore the wallet fraud architecture framework in practice.